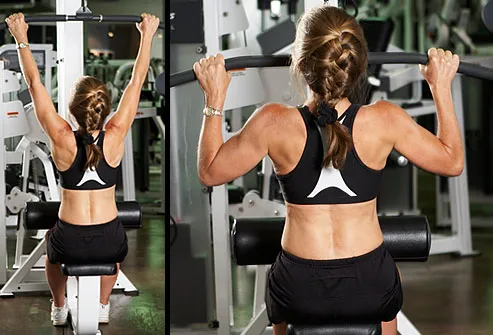No. 1: Walking
Why it's a winner: You can walk anywhere, anytime. Use a treadmill or hit the streets. All you need is a good pair of shoes.
How to: If you're just starting to walk for fitness, begin with five to 10 minutes at a time. Add a few minutes to each walk until you get to at least 30 minutes per walk. Then, quicken your pace or add hills.
No. 2: Interval Training
Why it's a winner: Interval training boosts your fitness levels and burns more calories to help you lose weight. The basic idea is to vary the intensity within your workout, instead of going at a steady pace.
How to: Whether you walk, run, dance, or do another cardio exercise, push up the pace for a minute or two. Then back off for 2 to 4 minutes. Exactly how long your interval should last depends on the length of your workout and how much recovery time you need. A trainer can fine-tune the pacing.. Repeat the intervals throughout your workout.
No. 3: Squats
Why it's a winner: Squats work several muscle groups -- your quadriceps ("quads"), hamstrings, and gluteals ("glutes") -- at the same time.
How to: Keep your feet shoulder-width apart and your back straight. Bend your knees and lower your rear as if you were sitting down in a chair. Keep your knees right over your ankles. Add dumbbells once you can do at least 12 reps with good form.
Squats Done Right
Practice with a real chair to master this move. First, sit all the way down in the chair and stand back up. Next, barely touch the chair's seat before standing back up. Work up to doing the squats without a chair, keeping the same form.
No. 4: Lunges
Why it's a winner: Like squats, lunges work all the major muscles of your lower body. They can also improve your balance.
How to: Take a big step forward, keeping your back straight. Bend your front knee to about 90 degrees. Keep weight on your back toes and drop the back knee toward the floor. Don't let the back knee touch the floor.
Lunges: Extra Challenge
Try stepping not just forward, but also back and out to each side, with each lunge. Add dumbbells to lunges once your form is down pat.
No. 5: Push-Ups
Why it's a winner: Push-ups strengthen your chest, shoulders, triceps, and core muscles.
How to: Facing down, place your hands slightly wider than shoulder-width apart. Place your toes on the floor. If that's too hard, start with your knees on the floor. Your body should make a straight line from shoulders to knees or feet. Keep your rear-end muscles and abs engaged. Bend your elbows to lower down until you almost touch the floor. Lift back up by pushing through your elbows, Keep your torso in a straight line throughout the move.
Push-Ups: Too Hard? Too Easy?
If you're new to push-ups you can start doing them by leaning into a kitchen counter. As you get stronger, go lower, using a desk or chair. Then you can move onto the floor, starting with your knees bent. For a challenge, put your feet on a stair, bench, or couch while keeping good form.
Crunches -- Method A
Start by lying on your back with your feet flat on the floor and your head resting in your palms. Press your lower back down. Contract your abdominal muscles (abs) and in one smooth move, raise your head, then your neck, shoulders, and upper back off the floor. Tuck in your chin slightly. Lower back down and repeat.
Crunches -- Method B
You can also do crunches with your feet off the floor and knees bent. This technique may keep you from arching your back. It also uses your hip flexors (muscles on your upper thighs below your hip bones).
Mastering Crunches
Keep your neck in line with your spine. Tuck in your chin so it doesn't stick out. Breathe normally. To keep chest and shoulders open, keep your elbows out of your line of vision.
No. 7: Bent-Over Row
Why it's a winner: You work all the major muscles of your upper back, as well as your biceps.
How to: Stand with your feet shoulder-width apart, bend your knees, and bend forward at the hips. Engage your abs without hunching your back. Hold weights beneath your shoulders, keeping your hands shoulder-width apart. Bend your elbows and lift both hands toward the sides of your body. Pause, then slowly lower your hands to the starting position. Can perform with a bar or dumbbells
Mastering Bent-Over Rows
First, do this move without weights so you learn the right motions. If you have trouble doing bent-over rows while standing up, support your weight by sitting on an incline bench, facing backward
 After releasing an Amazon Fire TV exclusive Flappy Birds Family,
Dong Nguyen is coming with a new game for smartphone users. Dubbed as
Swing Copters, the game will be launched tomorrow i.e. August 21 for
free in Google Play (and Apple Appstore).
After releasing an Amazon Fire TV exclusive Flappy Birds Family,
Dong Nguyen is coming with a new game for smartphone users. Dubbed as
Swing Copters, the game will be launched tomorrow i.e. August 21 for
free in Google Play (and Apple Appstore).